An Introduction to the Privacy Toolkit
Privacy and freedom of expression are fundamental human rights. People sharing personal data with your organization trust in your ability to handle their information with care.
Good privacy practices are not just a good idea – it’s the law and it’s mandatory for your organization to do business. You have the responsibility to ensure that data is accurate, used appropriately, and kept secure.
While the world of privacy can seem daunting, we are here to help. The Privacy Toolkit will establish your organization’s current threshold in privacy and security and help guide you to where you need to be!

The Privacy Toolkit is a joint initiative between Hewlett Packard Enterprise and Privacy by Design Centre of Excellence at Ryerson University.

What to expect
Through The Privacy Toolkit, you will:
- Complete a self-assessment of your current environment.
- Map how data flows within your organization.
- Learn practical guidance and procedures on how to ensure your organization is dealing with sensitive customer data in a safe and appropriate manner.
Why Do You Need to Care About Privacy?
People everywhere increasingly rely on information technology (IT) to manage their daily lives. They also expect their personal information to be protected. As an organization, you have the duty to ensure you responsibly manage the personal information you collect. Here are four reasons you need to take action today.
- Regulation: There is Canadian privacy legislation (the Personal Information Protection and Electronic Documents Act or PIPEDA 1) that sets out the ground rules for how businesses subject to the law must handle personal information in the course of commercial activities.
- External Stakeholder Demand: Your auditor or insurance company (and even your investors and customers) may ask you about how your business deals with privacy.
- Risk: One of your peers or competitors was hacked or involved in a privacy investigation by the regulator.
- First Mover Advantage: Dealing with privacy early is good for your business. By showing your leadership in this space, it will put you ahead of your competition

Why Embedding Privacy is Good for Your Business
Your business is accountable for the way you handle information. You need to have appropriate privacy and security practices that protect individuals from social, financial and physical harm that may come from the mismanagement of their personal information. At the same time, the organization needs to ensure that you are still able to achieve your business goals. A number of companies have been building programs where privacy is built into core business processes. This is called Privacy by Design and will be the basis for the toolkit.
What is Privacy by Design? In this video, Dr. Ann Cavoukian, global privacy expert and creator of Privacy by Design, will walk you through the framework.
The 7 Foundational Principles of Privacy by Design
These are the principles that should anchor anything your business does when personal information is involved. They aspire to go beyond compliance and reactive approaches to privacy and security risks. Good privacy doesn’t just happen by itself – it requires proactive and continuous goal-setting at the earliest stages.
The Privacy Toolkit Steps
It's time to get started on your journey through The Privacy Toolkit. Follow steps 1 to 5, answering the questions with your organization in mind.
The below figure is the Privacy and Security Maturity Scale. It represents the stages a company will go through on their privacy and security journey. Think about where your organization falls on this scale. This will help you assess where you are starting out and where you want to be in your approach to privacy and security. You should use this scale to chart and then track your progress.
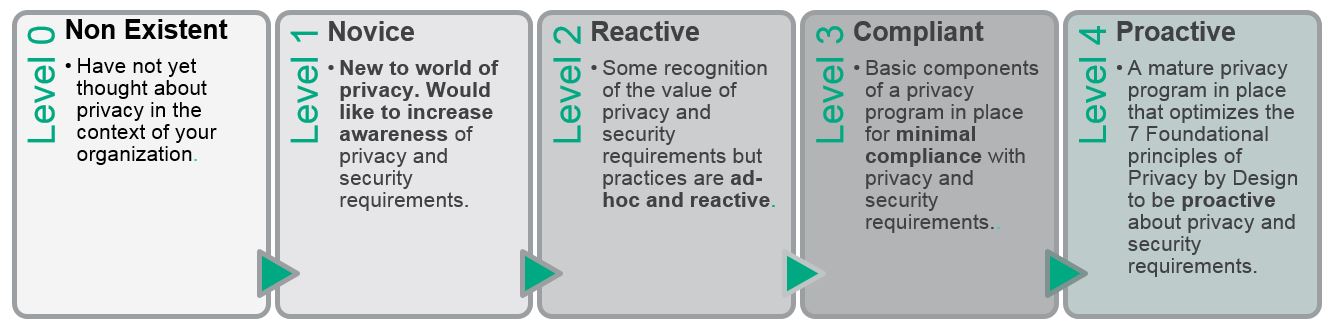
Note that while we hope this is a continual journey forward, you should continually visit and readdress where your organization is on the Privacy and Matrutiy Scale. In certain cases, events can cause companies to backslide (such as a change in management or personnel).
Click Here to Download the MatrixLet’s get to know some basics about your business before we start.
By completing this 5 minute company self-assessment, we will gauge the level of your organization’s privacy and security needs. Based on how you answer, you will be directed to a Privacy Checklist specific to your company’s needs.
The Checklist will walk you through thought-provoking questions for your business and provide links to further Tools and Resources.
Take the surveyNote: If you’ve already completed the Checklist, please proceed to Step 4
The Privacy Toolkit Checklist will walk you through questions based on the 7 Privacy by Design principles and associated actions you should be taking within your organization. By completing simple yes or no questions, you will:
- Identify the areas of privacy and security that need attention.
- Be provided tips and resources with regard to your needs.
Please complete the Company Assessment to identify which Checklist you should follow. Below are links to the various tracks.
Track 1:
Organization may do little or no interface with consumers. Personal information would be primarily employee data, perhaps mailing/distribution lists of company representatives or business clients, perhaps confidential/ proprietary information on clients.
Track 2:
Organization may have access to more personal information due to the nature of the product/service provided. Exposure to personal information will be more than just employee data but may be indirect through business clients.
Track 3:
Organization may handle more customer data compared to Tracks 1 and 2, thus requiring more sophisticated and perhaps more complex privacy and security controls, awareness / education.
Now that you’ve identified the key areas you are leading in and the areas you need to focus some additional attention, the next step is to clearly identify how data flows throughout your organization.
- Do you know how and where personally identifiable data enters into your organization, and how it flows throughout various departments?
- Do you know if the necessary permissions have been obtained to enable the use of the personal data by various departments, for additional purposes?
- Do you know if such data flows outside of your organization, to any third parties? Has additional consent been obtained to enable third parties to access such data?
In this exercise, you will look at how information flows within your business/organization, including any disclosures (information provided outside the organization). This tool will help you to complete a Data Map showing the flow of personal information through the system - from collection and use all the way to disclosures (sharing outside the organization) and destruction. This step will help to analyze and then assess privacy risks so that you can mitigate any potential for a privacy breach.
Here is a template that you can useThe attached file is fillable. You can download the attached file and save your changes to your computer.
Congratulations! You’ve completed the first round of The Privacy Toolkit. We hope you take the next step in utilizing the resources provided to develop and embed your own privacy program within your organization.
We want to stress the fact that privacy is a continual journey and it’s important to regularly reassess the status of your organization’s privacy program.
We suggest you make it an annual process to revisit The Privacy Toolkit to assess how your organization’s privacy and security program has matured. The intent is for your organization to evolve along the Privacy and Security Maturity Scale listed in Step 1. This way, you will be taking a proactive, Privacy by Design approach!
For additional tools and templates, please see the Resources section below.
Resources

Social Media Policy Template
This template will help draft and produce social media policies that can be applied to organizations of all sizes.

Educating Employees
Training employees on privacy is essential in every organization that handles personal information.

Sample Privacy Clause for Code of Conduct Agreement
It is common for new employees to sign a code of conduct agreement when they begin work. This template can be downloaded as a PDF and includes fillable text fields so that you can customize it for your organization.

Glossary of Definitions and Terms
Refer to this glossary to understand the terms that are used in the Toolkit.

Checklist Resources
Click here to see the full list of recommended resources from the Checklist.
About us
The Privacy Toolkit is a joint initiative between Hewlett Packard Enterprise and Privacy by Design Centre of Excellence at Ryerson University. Knowing that Canada is a land of small and medium businesses, HPE and Ryerson wanted to focus on creating a suite of resources to help raise education levels around privacy and security issues.
This toolkit was created by industry leaders and is available to you free of charge.
People everywhere increasingly rely on information technology to manage their daily lives. They also expect their personal information to be protected.
Hewlett Packard Enterprise understands the importance of privacy to the consumers and organizations. Our privacy strategy is based on providing transparency and choice for HPE customers worldwide. We create a chain of accountability for data privacy and security throughout our business and apply Privacy by Design in the product development process.
Our Privacy Office works with government agencies, lawmakers, regulators, nongovernmental organizations, and industry groups to encourage a more unified and robust approach to privacy regulation worldwide. While some variation by country is inevitable, we support more global interoperability of privacy regulations.
The Privacy by Design Centre of Excellence at Ryerson University a one-stop shop for all things associated with embedding privacy and security into the design of one’s operations, be they tech-related code, data architecture, IT, or involving policy, compliance or legal matters. Proactively identifying the potential risks and then embedding privacy-protective measures directly into your operations, right from the outset, can prevent the privacy harms from arising.
The Privacy by Design Centre of Excellence is led by Dr. Ann Cavoukian, the Distinguished Expert-in-Residence for Privacy and Data Analytics. Dr. Cavoukian is the creator of Privacy by Design's 7 Foundational Principles framework which has been included in the upcoming E.U. General Data Protection Regulation.
Dr. Ann Cavoukian is recognized as one of the world’s leading privacy experts. Appointed as the Information and Privacy Commissioner of Ontario, Canada in 1997, Dr. Cavoukian served an unprecedented three terms as Commissioner. During that time, she elevated the Office of the Information and Privacy Commissioner from a novice regulatory body to a first-class agency, known around the world for its cutting edge innovation and leadership.
We’d like to acknowledge the many organizations who helped in the development of The Privacy Toolkit:
Contact us
Need more assistance?
Speak with one of our experts about protecting your enterprise today.
Let's talk
Feedback
Let us know what you think about the Toolkit.
Feedback
1. The Privacy Toolkit acknowledges there is a variety of Privacy and Security legislation across Canada; however for the purposes of this Toolkit we are limiting the referencing to PIPEDA.